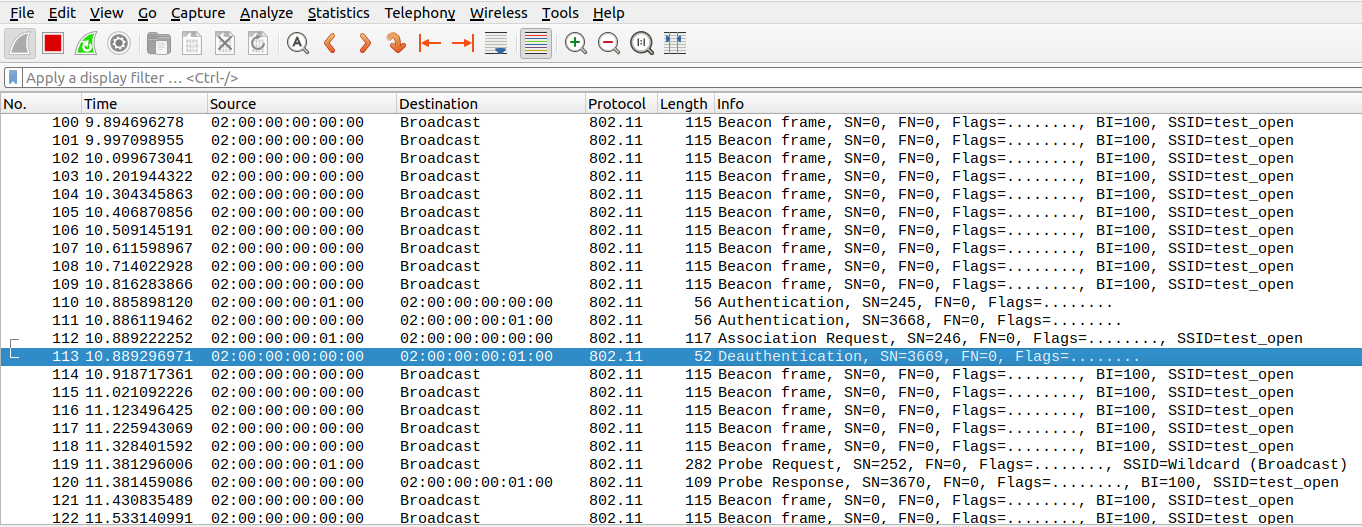
Q5-Deauth after assoc request
Topics in this section,
In this section, you are going to learn
How to send de-authentication packet on reception of association request packet from STA
# |
Version |
|---|---|
Ubuntu |
Ubuntu 22.04 64 bit |
Linux Kernel |
6.9.2 |
Hostapd |
hostapd 2.10 |
Send de-authentication packet on reception of authentication request packet from STA
Add a configuration parameter called “deauth_on_assoc_request_rx” in hostapd conf file
If “deauth_on_assoc_request_rx=0”, then this feature is disabled
If “deauth_on_assoc_request_rx=1”, then this feature is enabled
Call flow send de-authentication packet on reception of authentication request packet from STA
nl80211_global_init ()
wpa_driver_nl80211_init_nl_global ()
i802_init ()
wpa_driver_nl80211_drv_init ()
nl80211_init_bss ()
send_and_recv_msgs_connect_handle ()
process_global_event ()
do_process_drv_event ()
mlme_event ()
mlme_event_mgmt_tx_status ()
wpa_supplicant_event ()
process_bss_event ()
mlme_event ()
mlme_event_mgmt ()
wpa_supplicant_event ()
hostapd_mgmt_rx ()
ieee802_11_mgmt ()
handle_assoc ()
hostapd_drv_sta_deauth ()
Download the below patch file
send_deauth_after_assoc_req.patch
See the full content of patch file
diff -crB original/hostapd-2.10/hostapd/config_file.c changed/hostapd-2.10/hostapd/config_file.c
*** original/hostapd-2.10/hostapd/config_file.c 2022-01-17 02:21:29.000000000 +0530
--- changed/hostapd-2.10/hostapd/config_file.c 2024-07-26 15:27:14.464311339 +0530
***************
*** 2353,2359 ****
struct hostapd_bss_config *bss,
const char *buf, char *pos, int line)
{
! if (os_strcmp(buf, "interface") == 0) {
os_strlcpy(conf->bss[0]->iface, pos,
sizeof(conf->bss[0]->iface));
} else if (os_strcmp(buf, "bridge") == 0) {
--- 2353,2361 ----
struct hostapd_bss_config *bss,
const char *buf, char *pos, int line)
{
! if (os_strcmp(buf, "deauth_on_assoc_request_rx") == 0) {
! conf->deauth_on_assoc_request_rx = atoi(pos);
! } else if (os_strcmp(buf, "interface") == 0) {
os_strlcpy(conf->bss[0]->iface, pos,
sizeof(conf->bss[0]->iface));
} else if (os_strcmp(buf, "bridge") == 0) {
diff -crB original/hostapd-2.10/src/ap/ap_config.h changed/hostapd-2.10/src/ap/ap_config.h
*** original/hostapd-2.10/src/ap/ap_config.h 2022-01-17 02:21:29.000000000 +0530
--- changed/hostapd-2.10/src/ap/ap_config.h 2024-07-26 15:27:23.892311193 +0530
***************
*** 1100,1105 ****
--- 1100,1106 ----
unsigned int airtime_update_interval;
#define AIRTIME_MODE_MAX (__AIRTIME_MODE_MAX - 1)
#endif /* CONFIG_AIRTIME_POLICY */
+ int deauth_on_assoc_request_rx;
};
diff -crB original/hostapd-2.10/src/ap/ieee802_11.c changed/hostapd-2.10/src/ap/ieee802_11.c
*** original/hostapd-2.10/src/ap/ieee802_11.c 2022-01-17 02:21:29.000000000 +0530
--- changed/hostapd-2.10/src/ap/ieee802_11.c 2024-07-26 15:28:00.432310626 +0530
***************
*** 3589,3595 ****
mgmt->u.auth.variable[1] == WLAN_AUTH_CHALLENGE_LEN)
challenge = &mgmt->u.auth.variable[2];
! wpa_printf(MSG_DEBUG, "authentication: STA=" MACSTR " auth_alg=%d "
"auth_transaction=%d status_code=%d wep=%d%s "
"seq_ctrl=0x%x%s%s",
MAC2STR(mgmt->sa), auth_alg, auth_transaction,
--- 3589,3595 ----
mgmt->u.auth.variable[1] == WLAN_AUTH_CHALLENGE_LEN)
challenge = &mgmt->u.auth.variable[2];
! wpa_printf(MSG_INFO, "authentication: STA=" MACSTR " auth_alg=%d "
"auth_transaction=%d status_code=%d wep=%d%s "
"seq_ctrl=0x%x%s%s",
MAC2STR(mgmt->sa), auth_alg, auth_transaction,
***************
*** 5502,5512 ****
capab_info = le_to_host16(mgmt->u.assoc_req.capab_info);
listen_interval = le_to_host16(
mgmt->u.assoc_req.listen_interval);
! wpa_printf(MSG_DEBUG, "association request: STA=" MACSTR
" capab_info=0x%02x listen_interval=%d "
"seq_ctrl=0x%x%s",
MAC2STR(mgmt->sa), capab_info, listen_interval,
seq_ctrl, (fc & WLAN_FC_RETRY) ? " retry" : "");
left = len - (IEEE80211_HDRLEN + sizeof(mgmt->u.assoc_req));
pos = mgmt->u.assoc_req.variable;
}
--- 5501,5516 ----
capab_info = le_to_host16(mgmt->u.assoc_req.capab_info);
listen_interval = le_to_host16(
mgmt->u.assoc_req.listen_interval);
! wpa_printf(MSG_INFO, "association request: STA=" MACSTR
" capab_info=0x%02x listen_interval=%d "
"seq_ctrl=0x%x%s",
MAC2STR(mgmt->sa), capab_info, listen_interval,
seq_ctrl, (fc & WLAN_FC_RETRY) ? " retry" : "");
+ if(hapd->iconf->deauth_on_assoc_request_rx == 1) {
+ hostapd_drv_sta_deauth(hapd, mgmt->sa, WLAN_REASON_UNSPECIFIED);
+ return;
+ }
+
left = len - (IEEE80211_HDRLEN + sizeof(mgmt->u.assoc_req));
pos = mgmt->u.assoc_req.variable;
}
test:~$ pwd
/home/test
Make sure internet is available in laptop to download hostapd package
test:~$ sudo wget http://w1.fi/releases/hostapd-2.10.tar.gz
Create a directory
test:~$ mkdir hostapd
Change directory to hostapd
test:~$ cd hostapd
Note : Your present working directory should be hostapd
test:~$ pwd
/home/test/hostapd/
Extract hostapd
test:~$ sudo tar -xvf ~/hostapd-2.10.tar.gz
Run the below command to apply patch
test:~$ patch -p1 < send_deauth_after_assoc_req.patch
patching file hostapd-2.10/hostapd/config_file.c
patching file hostapd-2.10/src/ap/ap_config.h
patching file hostapd-2.10/src/ap/ieee802_11.c
Change directory to hostapd
test:~$ cd hostapd-2.10/hostapd/
Check the current working directory using pwd command
Make sure your current working directory is hostapd
test:~$ pwd
/home/test/hostapd/hostapd-2.10/hostapd/
Copy the contents of defconfig file to .config file
test:~$ sudo cp defconfig .config
Compile hostapd
test:~$ sudo make
Create run_hostapd.conf
test:~$ sudo vim ./run_hostapd.conf
ctrl_interface=/run/hostapd
interface=wlan0
driver=nl80211
ssid=test_open
hw_mode=g
channel=6
macaddr_acl=0
auth_algs=1
ignore_broadcast_ssid=0
deauth_on_assoc_request_rx=1
Run hostapd
test:~$ sudo ./hostapd ./run_hostapd.conf