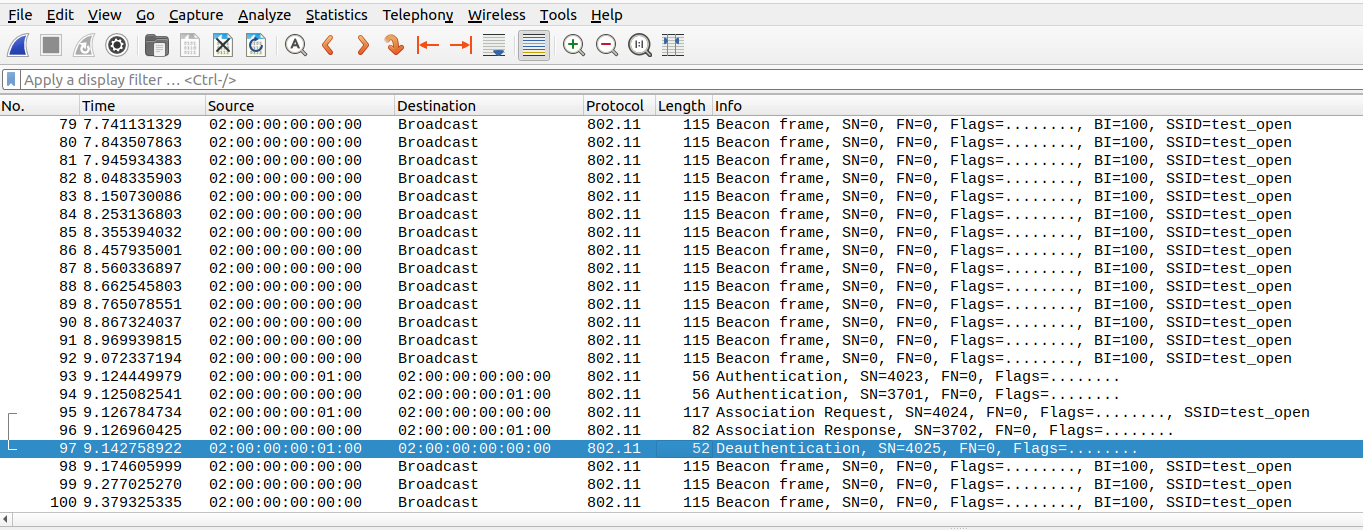
Q6-Deauth after assoc response
Topics in this section,
In this section, you are going to learn
How to send de-authentication packet on reception of association response packet from AP
# |
Version |
|---|---|
Ubuntu |
Ubuntu 22.04 64 bit |
Linux Kernel |
6.9.2 |
Supplicant |
wpa_supplicant 2.10 |
Send De-Authentication packet on reception of Association response packet from AP
Add a configuration parameter called “deauth_on_assoc_response_rx” in supplicant conf file
If “deauth_on_assoc_response_rx=0”, then this feature is disabled
If “deauth_on_assoc_response_rx=1”, then this feature is enabled
Call flow for send de-authentication packet on reception of association response packet from AP
nl80211_global_init ()
wpa_driver_nl80211_init_nl_global ()
process_global_event ()
do_process_drv_event ()
send_scan_event ()
process_global_event ()
do_process_drv_event ()
mlme_event ()
mlme_event_auth ()
wpa_supplicant_event ()
wpa_supplicant_event_assoc ()
wpa_supplicant_deauthenticate ()
Download the below patch file
send_deauth_after_assoc_res.patch
See the full content of patch file
diff -crB original/wpa_supplicant-2.10/wpa_supplicant/config_file.c changed/wpa_supplicant-2.10/wpa_supplicant/config_file.c
*** original/wpa_supplicant-2.10/wpa_supplicant/config_file.c 2022-01-17 02:21:29.000000000 +0530
--- changed/wpa_supplicant-2.10/wpa_supplicant/config_file.c 2024-07-25 17:42:21.365526245 +0530
***************
*** 329,335 ****
}
while (wpa_config_get_line(buf, sizeof(buf), f, &line, &pos)) {
! if (os_strcmp(pos, "network={") == 0) {
ssid = wpa_config_read_network(f, &line, id++);
if (ssid == NULL) {
wpa_printf(MSG_ERROR, "Line %d: failed to "
--- 329,338 ----
}
while (wpa_config_get_line(buf, sizeof(buf), f, &line, &pos)) {
! if (os_strncmp(pos, "deauth_on_assoc_response_rx=",28) == 0) {
! config->deauth_on_assoc_response_rx = atoi(pos+28);;
!
! } else if (os_strcmp(pos, "network={") == 0) {
ssid = wpa_config_read_network(f, &line, id++);
if (ssid == NULL) {
wpa_printf(MSG_ERROR, "Line %d: failed to "
diff -crB original/wpa_supplicant-2.10/wpa_supplicant/config.h changed/wpa_supplicant-2.10/wpa_supplicant/config.h
*** original/wpa_supplicant-2.10/wpa_supplicant/config.h 2022-01-17 02:21:29.000000000 +0530
--- changed/wpa_supplicant-2.10/wpa_supplicant/config.h 2024-07-25 17:39:17.477529099 +0530
***************
*** 1699,1704 ****
--- 1699,1705 ----
#endif /* CONFIG_TESTING_OPTIONS */
#endif /* CONFIG_PASN*/
+ int deauth_on_assoc_response_rx;
};
diff -crB original/wpa_supplicant-2.10/wpa_supplicant/events.c changed/wpa_supplicant-2.10/wpa_supplicant/events.c
*** original/wpa_supplicant-2.10/wpa_supplicant/events.c 2022-01-17 02:21:29.000000000 +0530
--- changed/wpa_supplicant-2.10/wpa_supplicant/events.c 2024-07-25 17:39:38.389528774 +0530
***************
*** 3298,3303 ****
--- 3298,3307 ----
return;
}
+ if(wpa_s->conf->deauth_on_assoc_response_rx == 1) {
+ wpa_supplicant_deauthenticate(wpa_s, WLAN_REASON_UNSPECIFIED);
+ return;
+ }
wpa_supplicant_set_state(wpa_s, WPA_ASSOCIATED);
if (os_memcmp(bssid, wpa_s->bssid, ETH_ALEN) != 0) {
if (os_reltime_initialized(&wpa_s->session_start)) {
***************
*** 3310,3316 ****
wpas_notify_auth_changed(wpa_s);
os_get_reltime(&wpa_s->session_start);
}
! wpa_dbg(wpa_s, MSG_DEBUG, "Associated to a new BSS: BSSID="
MACSTR, MAC2STR(bssid));
new_bss = 1;
random_add_randomness(bssid, ETH_ALEN);
--- 3314,3320 ----
wpas_notify_auth_changed(wpa_s);
os_get_reltime(&wpa_s->session_start);
}
! wpa_dbg(wpa_s, MSG_INFO, "Associated to a new BSS: BSSID="
MACSTR, MAC2STR(bssid));
new_bss = 1;
random_add_randomness(bssid, ETH_ALEN);
diff -crB original/wpa_supplicant-2.10/wpa_supplicant/sme.c changed/wpa_supplicant-2.10/wpa_supplicant/sme.c
*** original/wpa_supplicant-2.10/wpa_supplicant/sme.c 2022-01-17 02:21:29.000000000 +0530
--- changed/wpa_supplicant-2.10/wpa_supplicant/sme.c 2024-07-25 17:39:51.429528572 +0530
***************
*** 1550,1556 ****
return;
}
! wpa_dbg(wpa_s, MSG_DEBUG, "SME: Authentication response: peer=" MACSTR
" auth_type=%d auth_transaction=%d status_code=%d",
MAC2STR(data->auth.peer), data->auth.auth_type,
data->auth.auth_transaction, data->auth.status_code);
--- 1550,1556 ----
return;
}
! wpa_dbg(wpa_s, MSG_INFO, "SME: Authentication response: peer=" MACSTR
" auth_type=%d auth_transaction=%d status_code=%d",
MAC2STR(data->auth.peer), data->auth.auth_type,
data->auth.auth_transaction, data->auth.status_code);
diff -crB original/wpa_supplicant-2.10/wpa_supplicant/wpa_supplicant.c changed/wpa_supplicant-2.10/wpa_supplicant/wpa_supplicant.c
*** original/wpa_supplicant-2.10/wpa_supplicant/wpa_supplicant.c 2022-01-17 02:21:29.000000000 +0530
--- changed/wpa_supplicant-2.10/wpa_supplicant/wpa_supplicant.c 2024-07-25 17:38:51.545529501 +0530
***************
*** 4116,4122 ****
union wpa_event_data event;
int zero_addr = 0;
! wpa_dbg(wpa_s, MSG_DEBUG, "Request to deauthenticate - bssid=" MACSTR
" pending_bssid=" MACSTR " reason=%d (%s) state=%s",
MAC2STR(wpa_s->bssid), MAC2STR(wpa_s->pending_bssid),
reason_code, reason2str(reason_code),
--- 4116,4122 ----
union wpa_event_data event;
int zero_addr = 0;
! wpa_dbg(wpa_s, MSG_INFO, "Request to deauthenticate - bssid=" MACSTR
" pending_bssid=" MACSTR " reason=%d (%s) state=%s",
MAC2STR(wpa_s->bssid), MAC2STR(wpa_s->pending_bssid),
reason_code, reason2str(reason_code),
test:~$ pwd
/home/test
Make sure internet is available in laptop to download supplicant package
test:~$ sudo wget https://w1.fi/releases/wpa_supplicant-2.10.tar.gz
Create a directory
test:~$ mkdir supplicant
Change directory to supplicant
test:~$ cd supplicant
Note : Your present working directory should be supplicant
test:~$ pwd
/home/test/supplicant/
Extract wpa_supplicant
test:~$ sudo tar -xvf ~/wpa_supplicant-2.10.tar.gz
Run the below command to apply patch
test:~$ patch -p1 < send_deauth_after_assoc_res.patch
patching file wpa_supplicant-2.10/wpa_supplicant/config_file.c
patching file wpa_supplicant-2.10/wpa_supplicant/config.h
patching file wpa_supplicant-2.10/wpa_supplicant/events.c
patching file wpa_supplicant-2.10/wpa_supplicant/sme.c
patching file wpa_supplicant-2.10/wpa_supplicant/wpa_supplicant.c
Change directory to wpa_supplicant
test:~$ cd wpa_supplicant-2.10/wpa_supplicant/
Check the current working directory using pwd command
Make sure your current working directory is wpa_supplicant
test:~$ pwd
/home/test/supplicant/wpa_supplicant-2.10/wpa_supplicant
Copy the contents of defconfig file to .config file
test:~$ sudo cp defconfig .config
Compile wpa_supplicant
test:~$ sudo make
Create run_supplicant.conf
test:~$ sudo vim ./run_supplicant.conf
ctrl_interface=/run/wpa_supplicant
update_config=1
deauth_on_assoc_response_rx=1
network={
ssid="test_open"
key_mgmt=NONE
}
Run wpa_supplicant
test:~$ sudo ./wpa_supplicant -Dnl80211 -i wlan1 -c ./run_supplicant.conf
Download file to check wireshark output
send_deauth_after_assoc_res.pcapng
Check for deauthentication packet
Check packet No.96 and 97
Observe 96 is association response packet and 97 is deauthentication packet